The MITRE ATT&CK Framework
The MITRE ATT&CK Framework (Adversarial Tactics, Techniques, and Common Knowledge) is a globally recognized knowledge base that maps out the tactics and techniques used by threat actors throughout the cyber kill chain. Unlike traditional models that focus purely on prevention, ATT&CK focuses on what adversaries actually do once inside your network — from initial access to data exfiltration.
For incident responders and threat hunters, ATT&CK acts as a shared language and playbook for identifying, tracking, and mitigating malicious activity. It transforms reactive security into proactive defense by aligning detection logic, alert triage, and hunt methodologies with real-world adversarial behavior.
Why MITRE ATT&CK Matters
- Standardized Adversary Knowledge: ATT&CK provides a consistent way to describe attacker behaviors across campaigns, making it easier to compare incidents and share intelligence across teams and organizations.
- Bridges the Gap Between Detection and Response: Each technique in ATT&CK correlates to observable behavior, enabling analysts to map SIEM alerts, EDR telemetry, or network logs directly to known threat patterns.
- Improves Communication: Using a shared framework ensures that security teams, leadership, and external partners are aligned on what’s happening during an attack and how to respond.
- Empowers Threat Hunting: Hunters can proactively search for indicators of specific ATT&CK techniques (like PowerShell misuse or credential dumping) rather than waiting for alerts to trigger.
Using ATT&CK During Incident Response
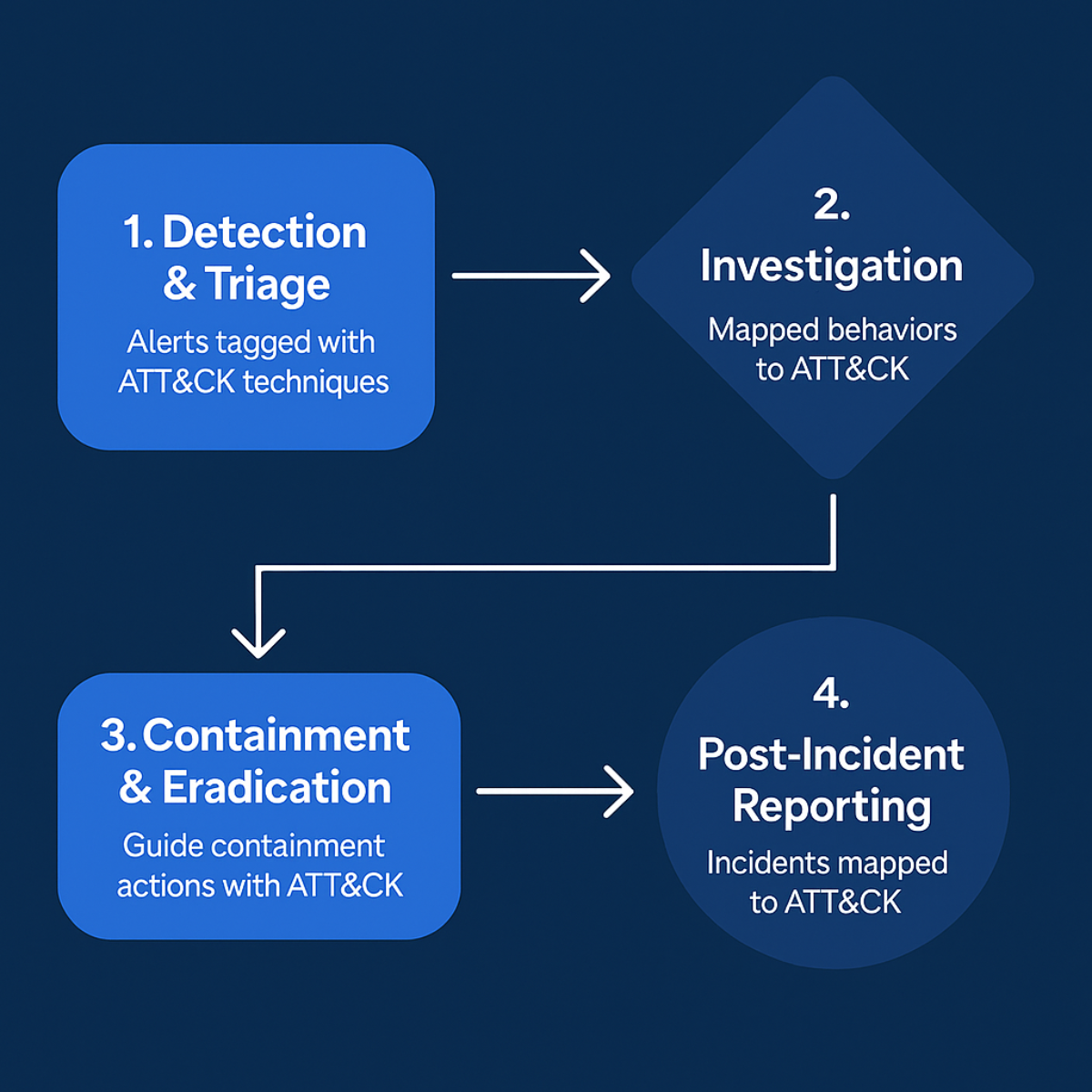
When an incident occurs, time is critical. The ATT&CK Framework gives responders a structured way to map out what has already happened, what the attacker’s next move might be, and where to look for evidence. Each phase of response benefits from ATT&CK alignment:
1. Detection & Triage
Alerts from EDR, SIEM, or IDS tools can be tagged with ATT&CK techniques (e.g., T1059 – Command and Scripting Interpreter or T1003 – Credential Dumping), giving immediate context to what type of behavior triggered the alert. This saves time and helps analysts quickly understand the intent behind the activity.
2. Investigation
By mapping observed behaviors to ATT&CK, responders can visualize the attacker’s progression through the environment. For example, seeing techniques like Execution via PowerShell followed by Persistence using Scheduled Tasks can indicate a lateral movement attempt. ATT&CK Navigator or similar tools help visualize this attack chain.
3. Containment & Eradication
ATT&CK helps guide containment actions by identifying which techniques are still active and which assets are compromised. Responders can focus on breaking the attacker’s chain of techniques — stopping privilege escalation or data exfiltration before it completes.
4. Post-Incident Reporting
Mapping incidents to ATT&CK not only improves post-incident documentation but also builds institutional knowledge. Future incidents become easier to detect and mitigate when previous ones are mapped to the same behavioral patterns.
Using ATT&CK for Threat Hunting
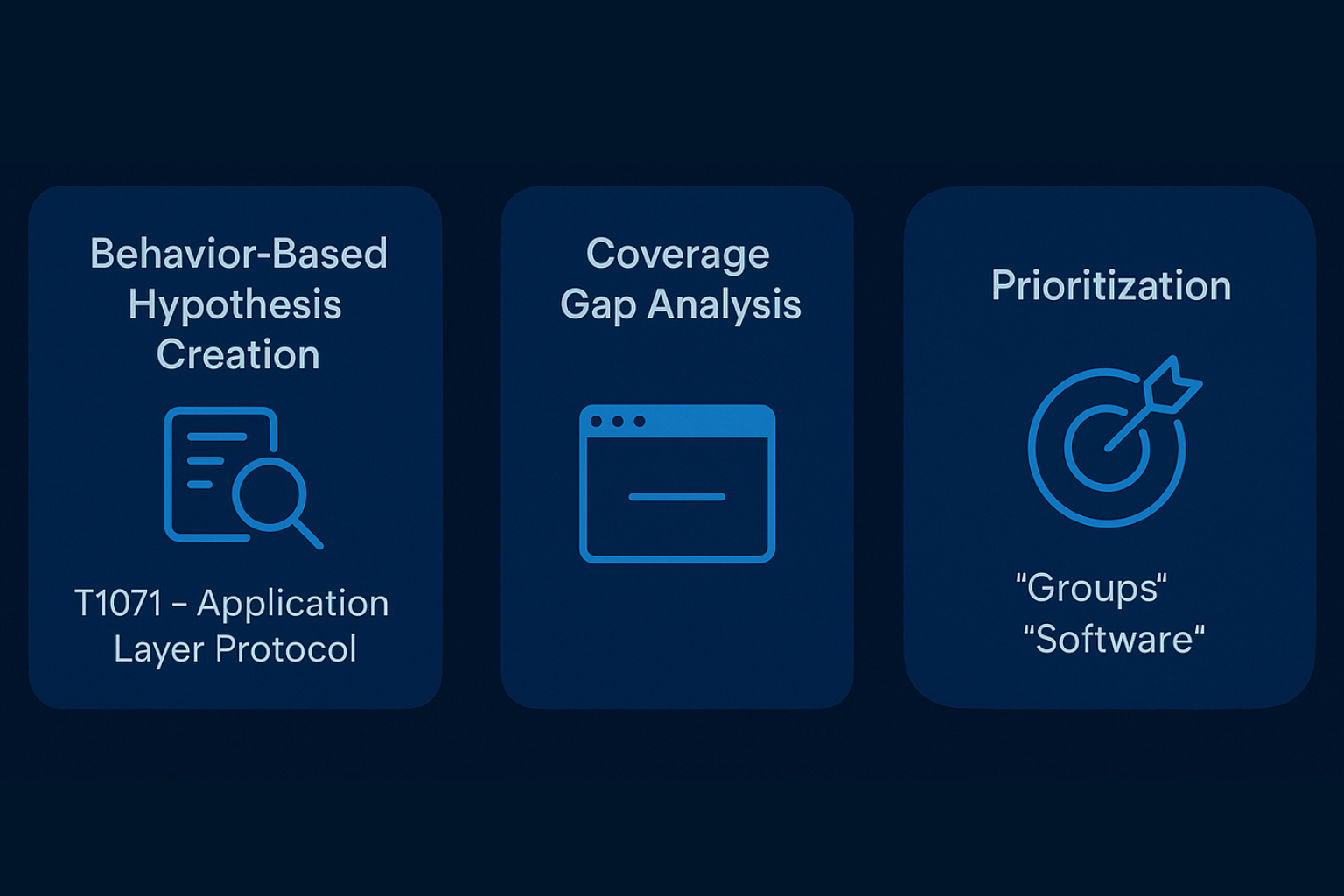
Threat hunting is the art of finding what your tools missed. ATT&CK empowers hunters by providing a blueprint of known adversarial techniques that can be used to craft hypotheses and hunting queries.
- Behavior-Based Hypothesis Creation: Hunters can start with a specific ATT&CK technique, such as T1071 – Application Layer Protocol, and develop KQL or Sigma queries to search logs for suspicious network communication.
- Coverage Gap Analysis: By reviewing which ATT&CK techniques are not currently being monitored, analysts can identify visibility blind spots and improve telemetry collection.
- Prioritization: Hunters can focus efforts on techniques known to be used by relevant threat groups targeting their sector (referencing ATT&CK’s “Groups” and “Software” mappings).
Regular hunts aligned with ATT&CK techniques create a feedback loop that improves both detection and prevention, helping security teams transition from reactive to proactive operations.
Practical Example
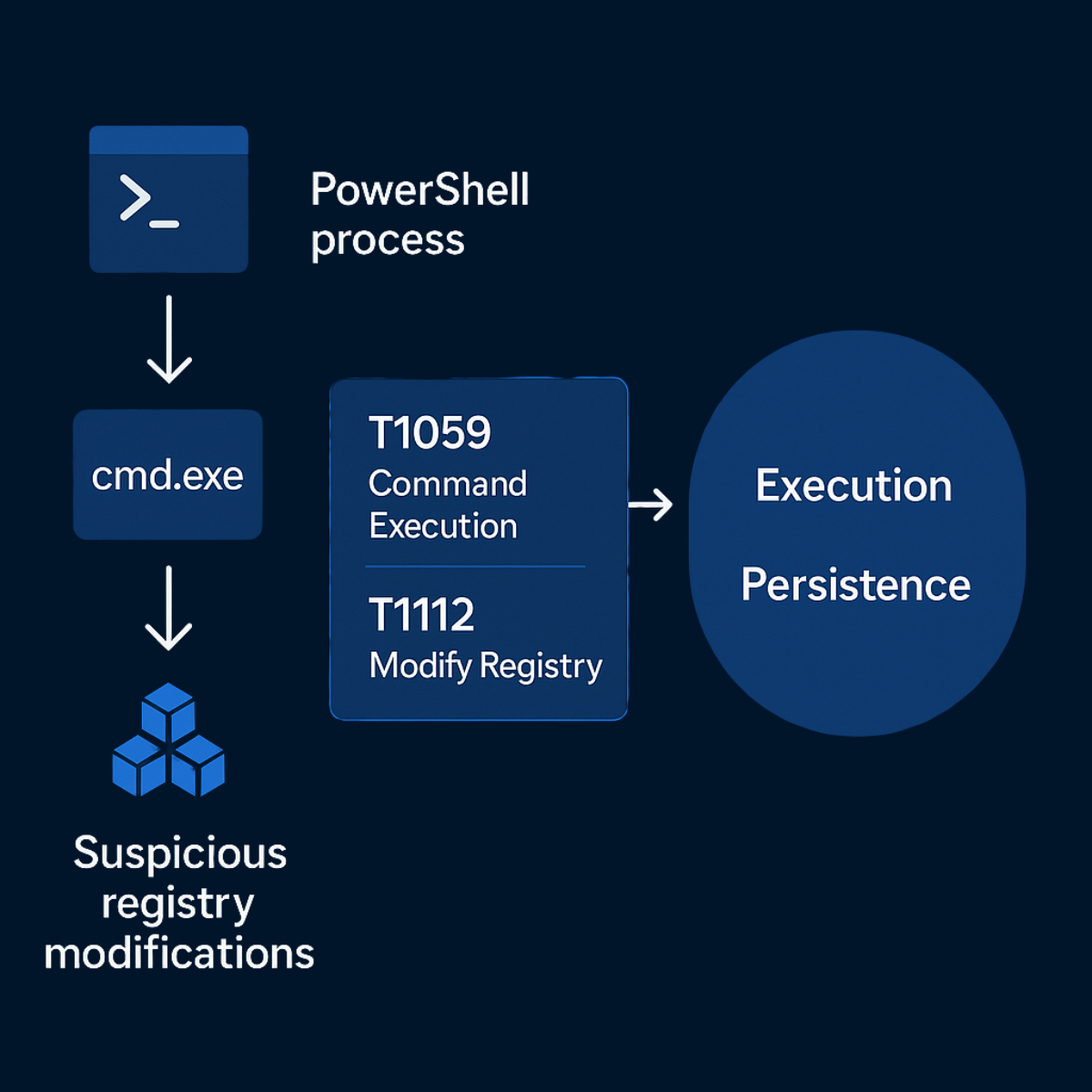
Imagine an analyst observes a PowerShell process spawning cmd.exe followed by suspicious registry modifications. Using ATT&CK, they can immediately identify these behaviors as T1059 (Command Execution) and T1112 (Modify Registry). This mapping provides instant insight into the adversary’s tactics — in this case, Execution and Persistence — and guides the next investigative steps, such as checking for lateral movement or persistence mechanisms.
Framework Integration
The MITRE ATT&CK Framework can be integrated into your existing security ecosystem:
- SIEM & EDR Mapping: Tag alerts with ATT&CK IDs to standardize investigation workflows.
- Threat Intelligence Correlation: Cross-reference observed techniques with known threat groups.
- Red vs. Blue Exercises: Use ATT&CK as a common language between offensive and defensive teams to test, measure, and improve detection capabilities.
Benefits of ATT&CK Alignment
- Improved Detection Engineering: Build analytics directly tied to adversarial behavior.
- Faster Incident Response: Analysts can recognize patterns more quickly and take targeted action.
- Enhanced Reporting: Leadership receives standardized, behavior-based insights rather than raw log data.
- Continuous Improvement: Feedback from hunts and incidents continually refines coverage maps.
Quick Checklist for Implementation
- Train your SOC team on MITRE ATT&CK terminology and structure.
- Integrate ATT&CK mappings into SIEM and EDR tools for context-rich alerts.
- Use ATT&CK Navigator to visualize detection coverage.
- Conduct threat hunts focused on specific ATT&CK techniques monthly.
- Map post-incident findings to ATT&CK to identify detection gaps.