Multifactor Authentication Best Practices
Multi-Factor Authentication (MFA) has become a cornerstone of modern identity and access management. With credential theft still being one of the leading causes of breaches, MFA adds an essential layer of protection by requiring more than one verification method to confirm user identity. However, MFA is not a "set it and forget it" control—its effectiveness depends on proper configuration, enforcement, and monitoring.
Core Best Practices
- 1. Enforce MFA for All Accounts — Especially Privileged Ones: Implement MFA across all users, but prioritize administrative and high-privilege accounts first. Compromising a privileged account can lead to full domain control, so MFA enforcement should start there and expand to all identities.
- 2. Avoid SMS-Based MFA When Possible: SMS and voice-based MFA are vulnerable to SIM swapping and social engineering attacks. Opt for stronger factors like authenticator apps (Microsoft Authenticator, Duo, Google Authenticator) or hardware keys (YubiKey, Titan).
- 3. Use Phishing-Resistant MFA Methods: Adopt modern standards such as FIDO2 and WebAuthn to protect against phishing attempts. These methods use public-key cryptography and are tied to specific devices, making credential theft far more difficult.
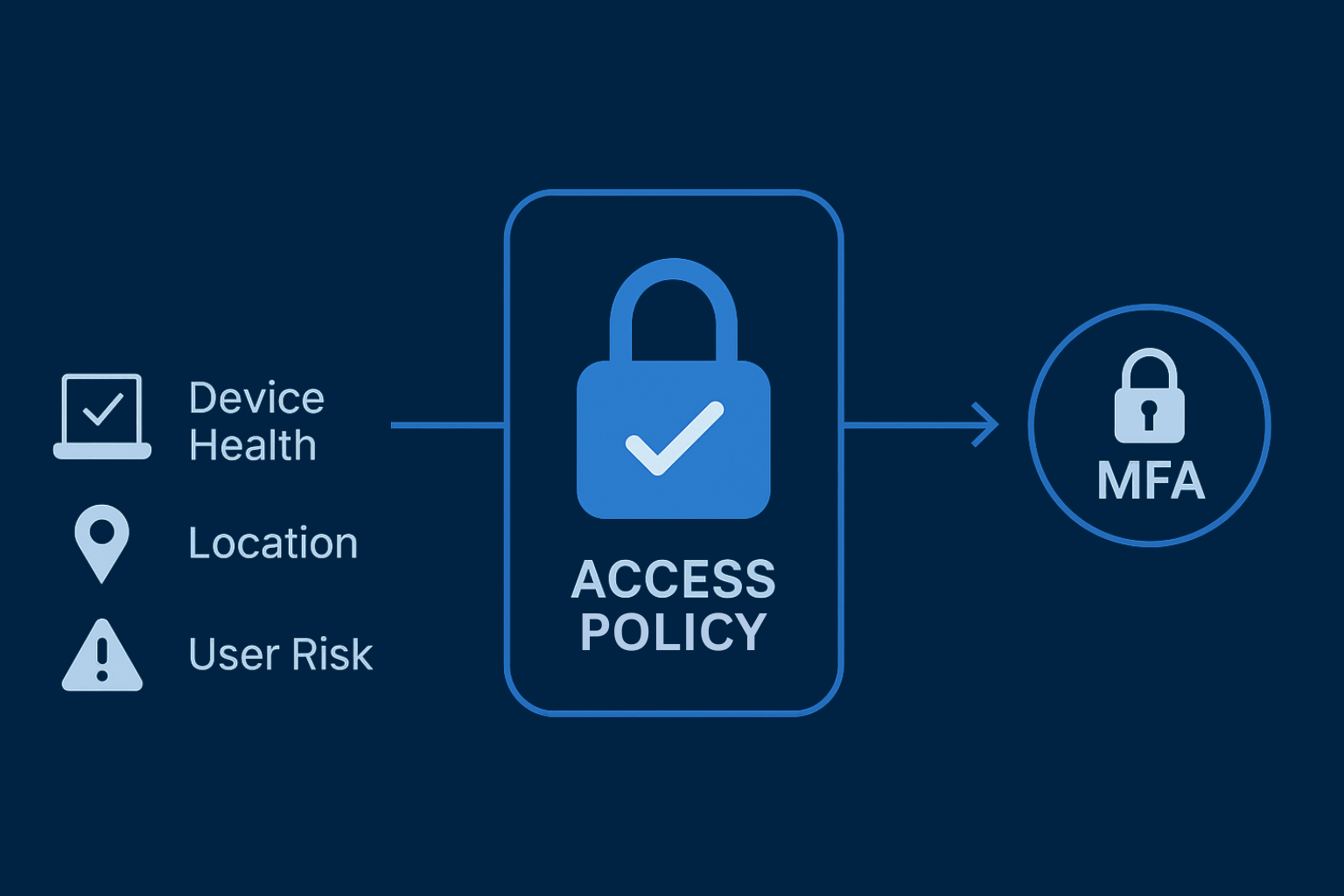
- 4. Apply Conditional Access Policies: Combine MFA with contextual signals such as device health, location, and user risk. For example, require MFA only when a user logs in from an untrusted device or foreign IP address.
- 5. Monitor and Respond to MFA Fatigue Attacks: Attackers often exploit user impatience by sending repeated MFA prompts (“push bombing”). Configure systems to detect this pattern and train users to recognize and report unusual MFA notifications.
- 6. Implement Strong Recovery Procedures: Account recovery is often a weak point in MFA deployments. Require identity verification steps before allowing recovery or reset of authentication methods, and log all recovery activity for auditing.
- 7. Educate Users Continuously: Technology alone isn’t enough. Regularly train users to identify phishing, report suspicious MFA prompts, and understand why MFA is critical to organizational security.

Framework Alignment
MFA best practices align with several established cybersecurity frameworks:
- NIST CSF: PR.AC-7 (Users are authenticated commensurate with risk of transactions)
- CIS Controls v8: Control 6 — Access Control Management
- Zero Trust Architecture: Verify explicitly and assume breach; MFA is a core enforcement mechanism
Implementation Recommendations
Deploy MFA in phases, starting with high-risk users, then expanding to all employees. Integrate MFA with Single Sign-On (SSO) for better user experience and central management. Regularly audit MFA enrollment reports to identify gaps, disabled users, or outdated devices.
Example rollout plan:
- Assess current authentication landscape and identify high-value targets.
- Select a secure MFA solution (preferably supporting FIDO2 and adaptive access).
- Run pilot programs with IT and executive teams before organization-wide rollout.
- Set policies for enforcement, timeout, and step-up authentication conditions.
- Continuously monitor authentication logs for anomalies.
Expected Outcomes
- Risk Reduction: Up to 99% reduction in credential-based compromises when MFA is properly enforced.
- Improved Compliance: Satisfies regulatory requirements under NIST, ISO 27001, and CMMC frameworks.
- Enhanced Visibility: Better insight into user authentication behaviors and potential threat patterns.

Key Lessons & Takeaways
- MFA is only as strong as its weakest factor—avoid SMS and rely on cryptographic solutions.
- Balance usability and security with adaptive policies.
- Train users frequently and incorporate MFA-related metrics into your security KPIs.