Understanding the NIST Risk Management Framework (RMF)
In cybersecurity, risk is inevitable — but unmanaged risk is unacceptable. The NIST Risk Management Framework (RMF), outlined in NIST Special Publication 800-37 Revision 2, provides a comprehensive, six-step process that integrates security and risk management activities into the system development life cycle.
Originally developed for federal agencies, the RMF is now widely adopted across private sectors for its ability to link technical safeguards with organizational mission and business priorities. It’s not just a compliance checklist — it’s a mindset that encourages proactive risk reduction through continuous monitoring, informed decision-making, and strong documentation.
Why the RMF Matters
- Structured Risk Management: RMF turns cybersecurity from a reactive exercise into a managed, measurable process.
- Integration Across Lifecycle: Security isn’t bolted on — it’s built in from system design through continuous monitoring.
- Supports Compliance: RMF maps directly to FISMA, FedRAMP, DoD RMF, and aligns with ISO 27001 principles.
- Promotes Informed Decision-Making: Risk decisions are based on impact analysis, threat data, and mission priorities rather than guesswork.
The Six Steps of the NIST RMF
1. Categorize the System
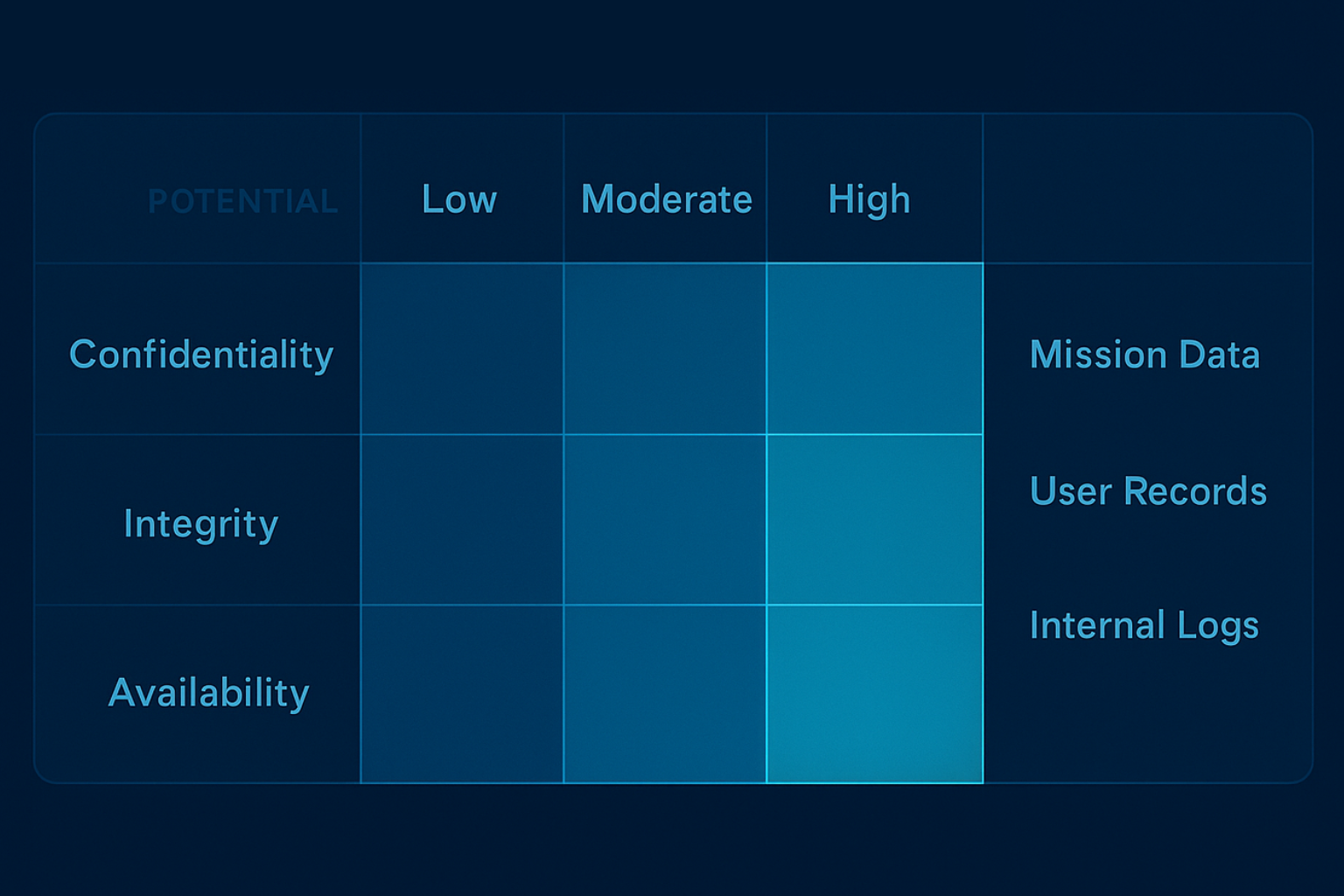
The first step is identifying and categorizing the system based on its potential impact on organizational operations, assets, or individuals. This step uses FIPS 199 and FIPS 200 to define security impact levels (Low, Moderate, or High) for confidentiality, integrity, and availability.
Goal: Understand what needs protection and how critical it is to mission success.
2. Select Security Controls
Once categorized, organizations select baseline security controls from NIST SP 800-53. These controls are then tailored based on system characteristics, risk tolerance, and regulatory requirements.
Goal: Apply appropriate safeguards that balance protection and operational needs.
3. Implement Security Controls
The selected controls are implemented and documented, detailing how each control is applied within the system. Implementation may include configurations, policies, and technical settings.
Goal: Ensure controls are operating as intended within the system environment.
4. Assess Security Controls
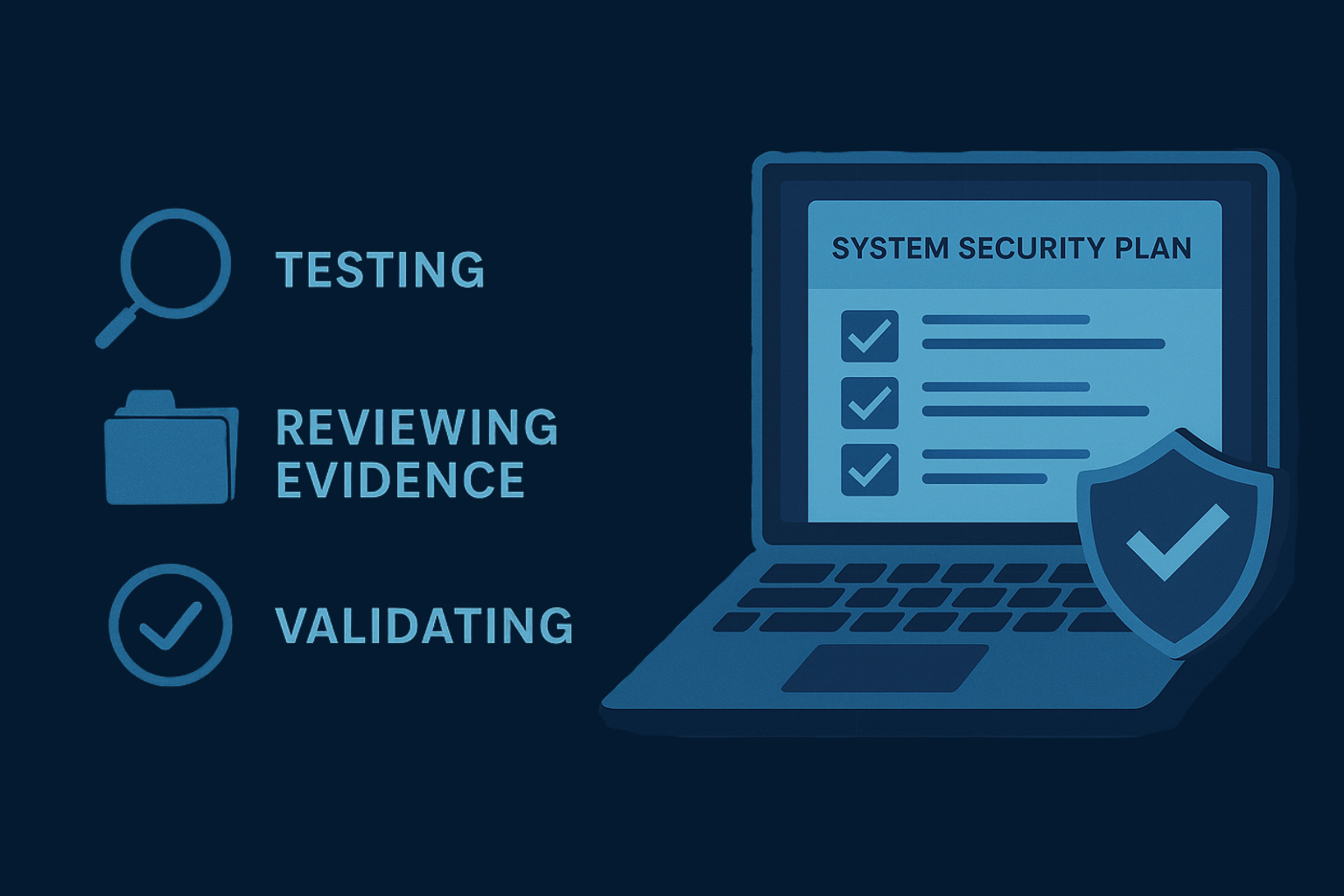
Assessors evaluate whether the implemented controls are effective in reducing risk. This involves testing, reviewing evidence, and validating that controls function as described in the system security plan (SSP).
Goal: Determine if the controls provide the required protection level for the system’s risk category.
5. Authorize the System
Senior officials review the assessment results to decide whether to authorize the system for operation. The authorization decision is based on the residual risk and whether it’s acceptable within the organization’s risk tolerance.
Goal: Obtain formal approval to operate, based on informed risk acceptance.
6. Monitor the System
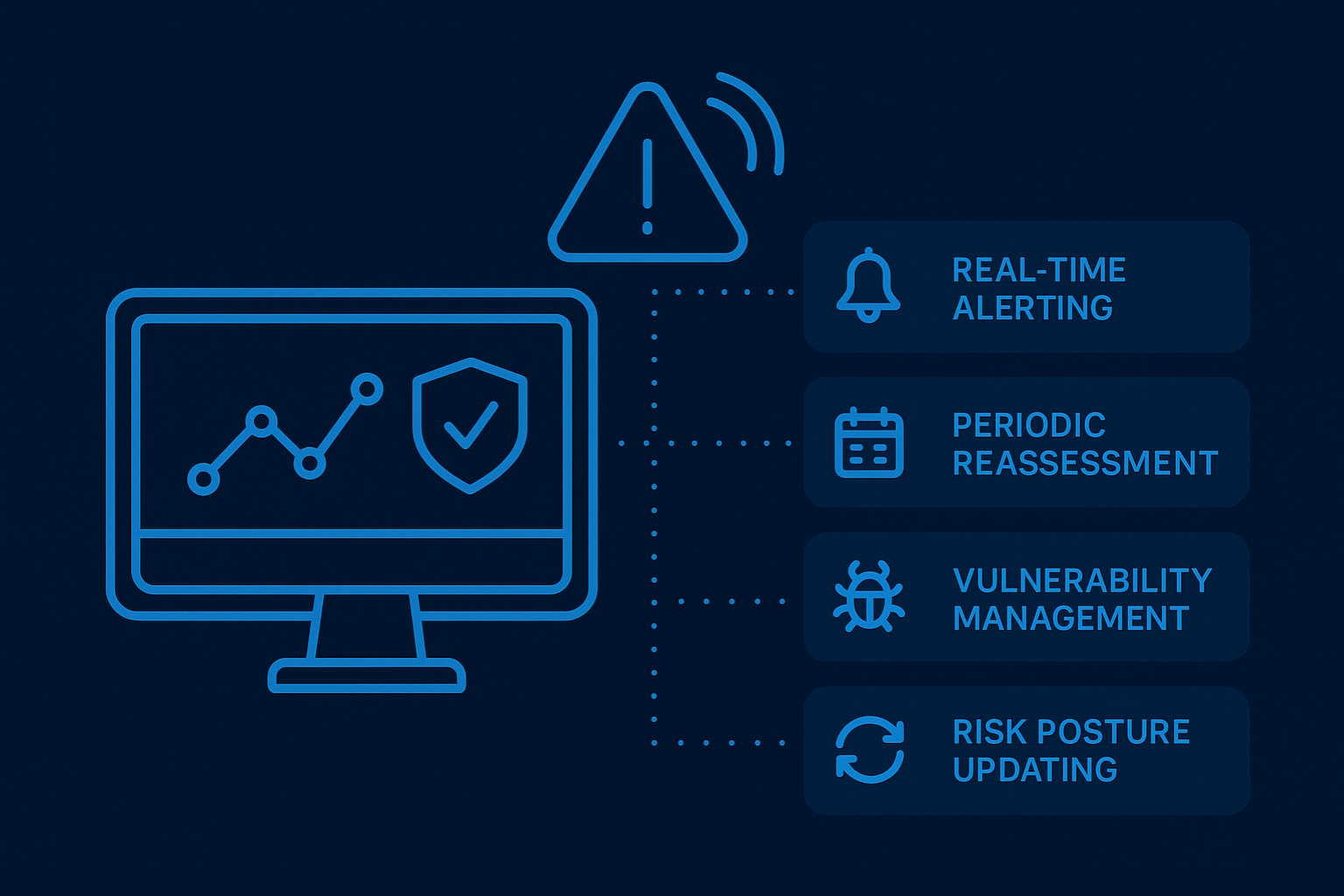
Continuous monitoring ensures that controls remain effective as threats evolve. This includes real-time alerting, periodic reassessment, vulnerability management, and updating the risk posture.
Goal: Maintain an adaptive and resilient security posture over time.
How RMF Supports Incident Response
During an incident, time and clarity are everything. RMF helps organizations respond more effectively by ensuring security controls are well-documented, understood, and mapped to their risk levels. This means that when an alert triggers, responders already know:
- Which controls protect the affected system
- What the expected system behavior is under normal operations
- Who the authorizing officials and response stakeholders are
RMF’s continuous monitoring phase also ensures that detection and response capabilities evolve in tandem with the threat landscape. It supports structured incident reporting and post-incident analysis, helping teams assess whether risk acceptance thresholds remain appropriate.
How RMF Enhances Threat Hunting
RMF encourages visibility. Through the documentation and assessment process, analysts gain a clear understanding of where data resides, which controls protect it, and what normal network behavior looks like. This context directly improves threat hunting operations.
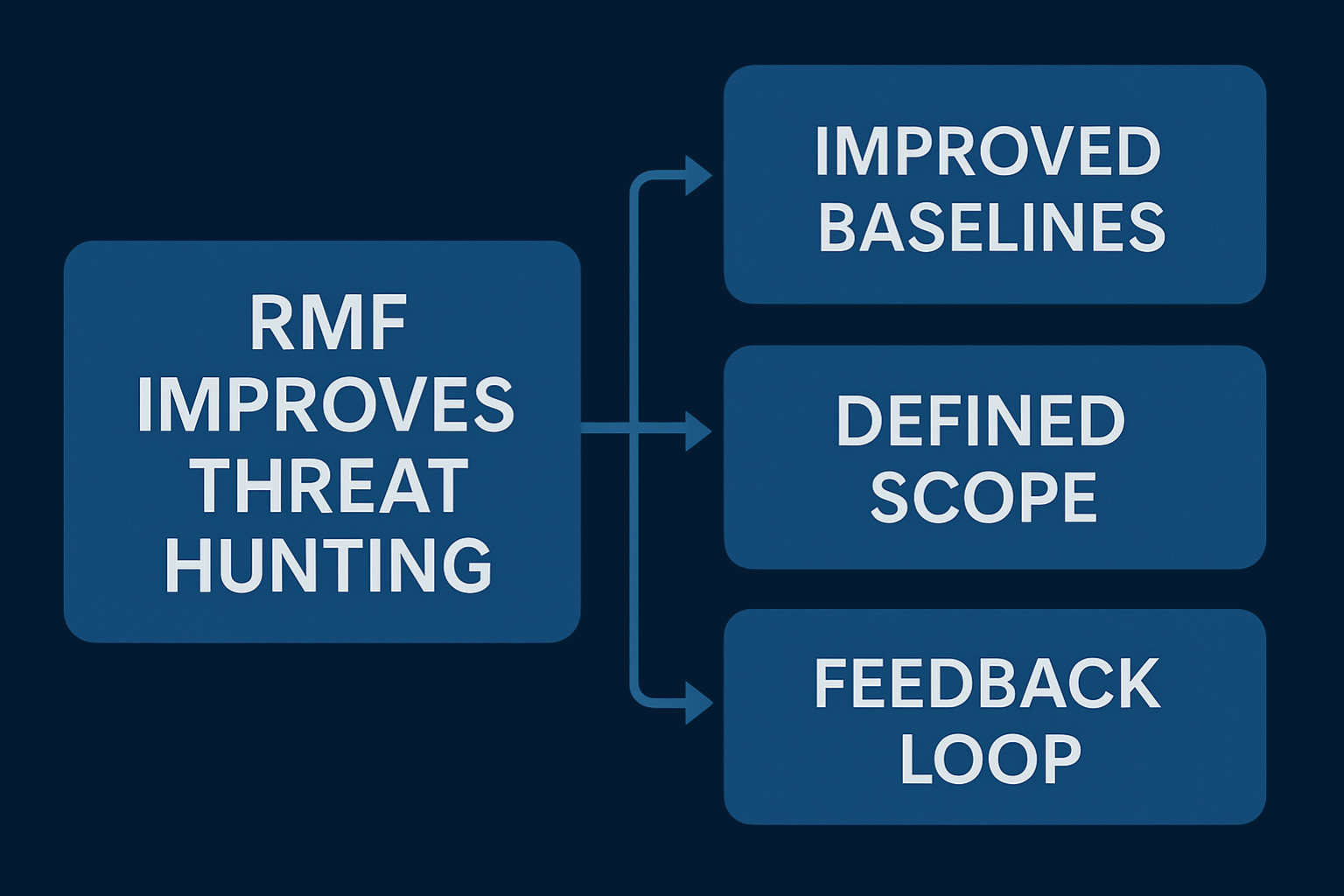
- Improved Baselines: Hunters can identify anomalies faster when baselines are established through continuous monitoring.
- Defined Scope: RMF documentation outlines systems, data flows, and assets, helping hunters focus on high-value targets.
- Feedback Loop: Findings from threat hunts can inform control enhancements and feed back into the RMF lifecycle.
Essentially, RMF gives hunters the map they need to explore — and secure — the digital terrain.
Benefits of Implementing RMF
- Standardization: Consistent methodology for risk management across all systems and teams.
- Accountability: Clearly defines roles and responsibilities for system owners, assessors, and authorizing officials.
- Improved Compliance: Demonstrates due diligence for federal and industry cybersecurity standards.
- Scalability: Works for organizations of all sizes and maturity levels, from startups to federal agencies.
- Proactive Defense: Encourages continuous improvement and anticipates threats before they become incidents.
Quick Checklist for RMF Implementation
- Categorize systems based on data sensitivity (FIPS 199)
- Select appropriate controls from NIST SP 800-53
- Document all control implementations in the SSP
- Conduct a thorough security assessment
- Obtain formal authorization to operate (ATO)
- Continuously monitor and update system posture